Introduction to CI/CD Pipelines
Continuous Integration and Continuous Deployment (CI/CD) have become essential practices in modern software development. A well-designed CI/CD pipeline automates the building, testing, and deployment of applications, reducing human error and accelerating delivery. In this comprehensive guide, we will explore the best practices for building reliable deployment workflows.
Understanding the CI/CD Philosophy
Continuous Integration (CI) is the practice of frequently merging code changes into a shared repository, where automated builds and tests verify each integration. This catches bugs early and reduces integration problems.
Continuous Deployment (CD) extends CI by automatically deploying every change that passes the test suite to production. Continuous Delivery is a similar concept where deployments are manual but always ready.
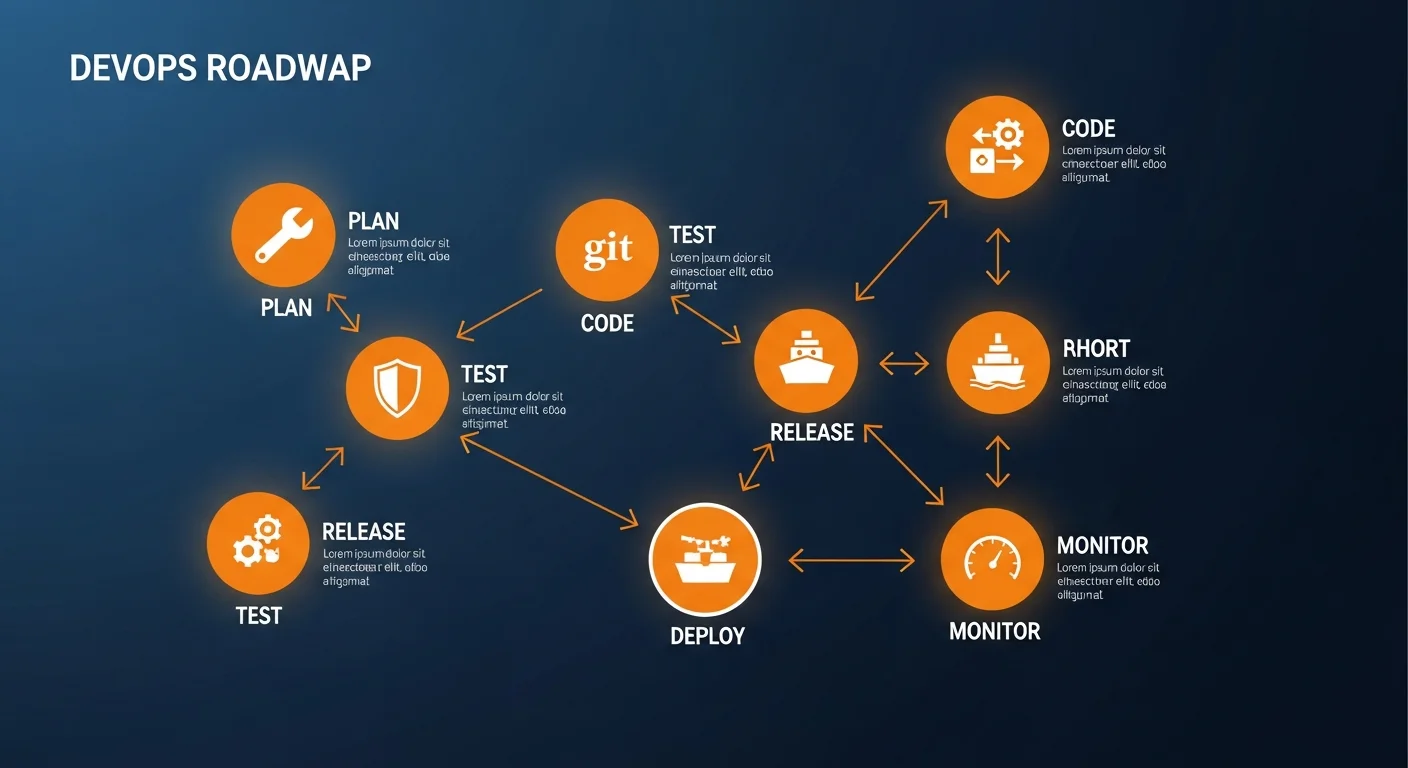
Core Components of a CI/CD Pipeline
A robust pipeline typically includes these stages:
- Source Control: Git repository as the single source of truth
- Build: Compiling code and creating artifacts
- Test: Running unit, integration, and end-to-end tests
- Security Scan: Static analysis and vulnerability scanning
- Deploy: Pushing to staging and production environments
- Monitor: Observing application health post-deployment
Best Practice 1: Keep Pipelines Fast
Pipeline speed directly impacts developer productivity. Slow pipelines discourage frequent commits and slow down feedback loops. Target these benchmarks:
- Unit tests: Under 5 minutes
- Integration tests: Under 15 minutes
- Full pipeline: Under 30 minutes
Optimization strategies:
# Parallel test execution
jobs:
test:
strategy:
matrix:
shard: [1, 2, 3, 4]
steps:
- run: npm test -- --shard=${{ matrix.shard }}/4
# Cache dependencies
- uses: actions/cache@v3
with:
path: node_modules
key: deps-${{ hashFiles('package-lock.json') }}Best Practice 2: Implement Comprehensive Testing
Your testing strategy should follow the testing pyramid:
Unit Tests (70%): Fast, isolated tests for individual functions and components. These form the foundation and run on every commit.
Integration Tests (20%): Test interactions between components, database operations, and API endpoints.
End-to-End Tests (10%): Full user journey tests that verify the complete application flow.
# Example test stage configuration
test:
stage: test
script:
- npm run test:unit
- npm run test:integration
- npm run test:e2e
coverage: '/Coverage: (\d+\.?\d*)%/'Best Practice 3: Use Infrastructure as Code
Define your infrastructure alongside your application code. This ensures consistency across environments and enables version control for infrastructure changes.
# Terraform example
resource "aws_instance" "app_server" {
ami = var.app_ami
instance_type = "t3.medium"
tags = {
Name = "production-app"
Environment = "production"
}
}Popular IaC tools include Terraform, Pulumi, AWS CloudFormation, and Ansible. Choose based on your cloud provider and team expertise.
Best Practice 4: Implement Security Scanning
Security should be integrated into every pipeline stage (shift-left security):
- SAST: Static Application Security Testing analyzes source code
- DAST: Dynamic testing against running applications
- Dependency Scanning: Check for vulnerable packages
- Container Scanning: Analyze Docker images for vulnerabilities
# Security scanning stage
security:
stage: test
parallel:
matrix:
- SCANNER: [sast, dependency_check, container_scan]
script:
- ./run-scanner.sh $SCANNERBest Practice 5: Use Environment Parity
Development, staging, and production environments should be as similar as possible. This reduces "works on my machine" problems and catches environment-specific issues early.
- Use containerization (Docker) for consistent environments
- Use the same database engine across all environments
- Mirror production data (anonymized) in staging
- Use environment variables for configuration differences
Best Practice 6: Implement Deployment Strategies
Choose the right deployment strategy based on your risk tolerance:
Rolling Deployment: Gradually replace instances with new versions. Good balance of speed and safety.
Blue-Green Deployment: Run two identical environments, switch traffic between them. Enables instant rollback.
Canary Deployment: Route a small percentage of traffic to the new version first. Best for high-risk changes.
# Kubernetes canary deployment
spec:
replicas: 10
strategy:
canary:
steps:
- setWeight: 10
- pause: {duration: 5m}
- setWeight: 50
- pause: {duration: 10m}
- setWeight: 100Best Practice 7: Automate Rollbacks
Even with thorough testing, production issues can occur. Automated rollbacks minimize downtime:
- Monitor key metrics after deployment (error rates, latency, CPU usage)
- Define automatic rollback triggers based on thresholds
- Keep previous versions ready for instant rollback
- Test your rollback procedure regularly
Best Practice 8: Maintain Pipeline as Code
Store your pipeline configuration in version control alongside application code. This provides:
- History of pipeline changes
- Code review for pipeline modifications
- Branch-specific pipeline configurations
- Easy replication across projects
Popular CI/CD Tools Comparison
GitHub Actions: Excellent for GitHub-hosted projects, generous free tier, extensive marketplace.
GitLab CI: Comprehensive DevOps platform, built-in container registry, auto DevOps features.
Jenkins: Highly customizable, vast plugin ecosystem, self-hosted control.
CircleCI: Fast, good Docker support, easy configuration.
Monitoring and Observability
A complete CI/CD practice includes post-deployment monitoring:
- Set up application performance monitoring (APM)
- Configure alerting for anomalies
- Track deployment frequency and failure rates
- Measure mean time to recovery (MTTR)
Conclusion
Building reliable CI/CD pipelines requires careful planning and continuous improvement. Start with the basics—automated testing and deployment—then gradually add security scanning, advanced deployment strategies, and comprehensive monitoring. Remember that CI/CD is a journey, not a destination. Regularly review and optimize your pipelines as your team and applications grow.
Looking to deepen your DevOps knowledge? Explore our curated collection of DevOps and cloud computing books to master these essential skills.